Prerequisites
Complete the steps outlined in the SCIM Directory Integration support article to set up a new SCIM user directory in your Kandji tenant. You will need to obtain the SCIM access token and API URL.
Copy and store the token provided outlined in the SCIM Directory Integration article. Once you click Done, the token will not be visible and will be required in a later step.
Be sure to review the supported user and group attributes listed in the SCIM Directory Integration.
Ensure that nested groups are not included with SCIM as Microsoft does not support this functionality.
Create the SCIM Integration in Microsoft Entra ID
Sign in to the Microsoft Entra admin center.
Open the portal menu and then select Entra ID.
On the Entra ID menu, under select Enterprise apps.
In the Manage section, select All applications.
Select New application. If you have already created a SAML single sign-on application, you can select that application and add SCIM.
.png)
Select Create your own application.
Give the application a name.
Select Integrate any other application you don't find in the gallery (Non-gallery).
Click Create.
.png)
You will be taken to the Overview page for the newly created app.
Under Manage, select Provisioning.
Click New Configuration.
.png)
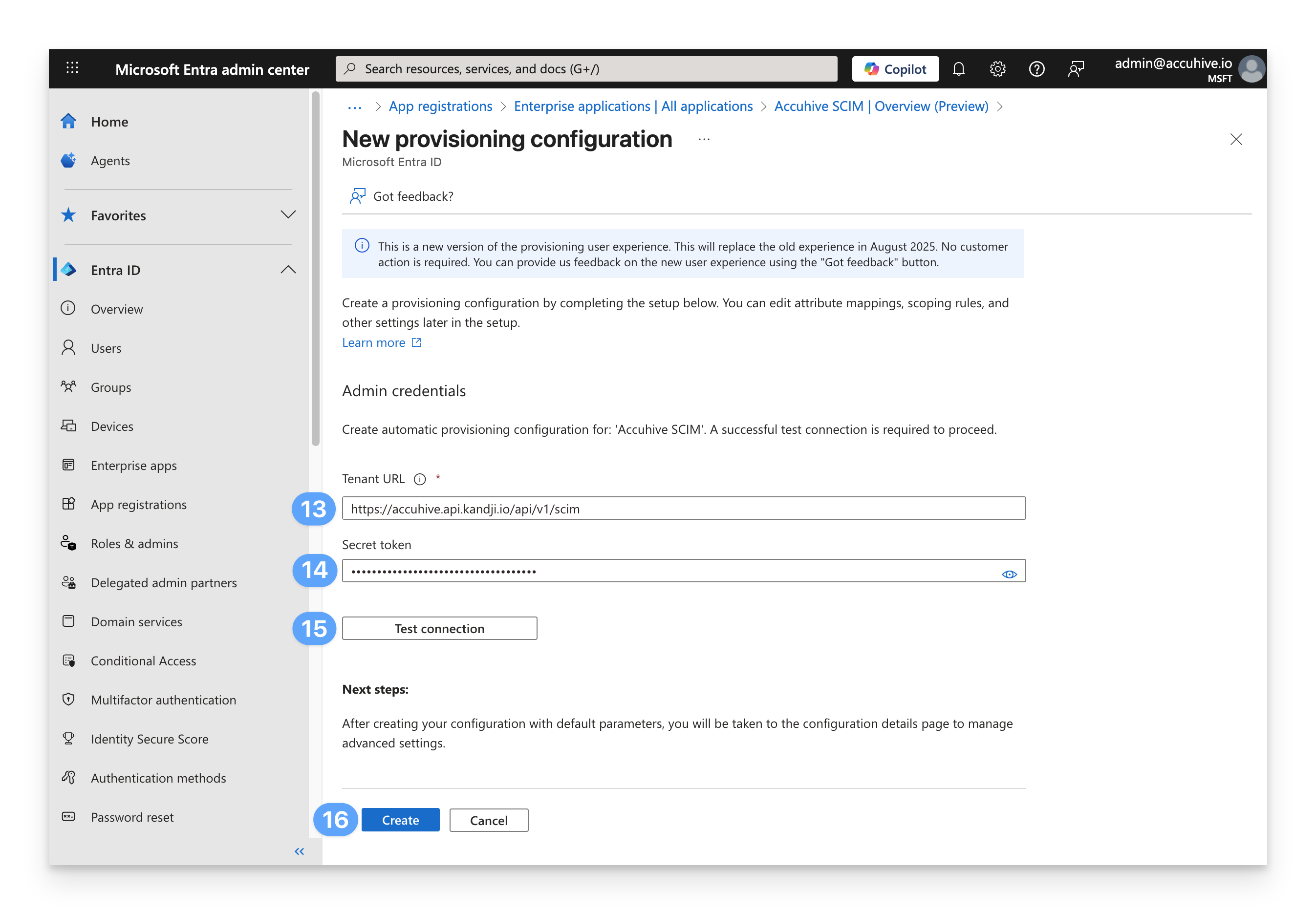
Paste the Kandji SCIM API URL that you copied earlier into the Tenant URL field.
Paste the API token that you copied earlier into the Secret token field.
Click Test connection. You should see a successful test notification.
Click Create.
Click on the Provisioning in the Manage section.
.png)
Expand the Mappings reveal triangle and ensure that both Groups and Users are enabled.
.png)
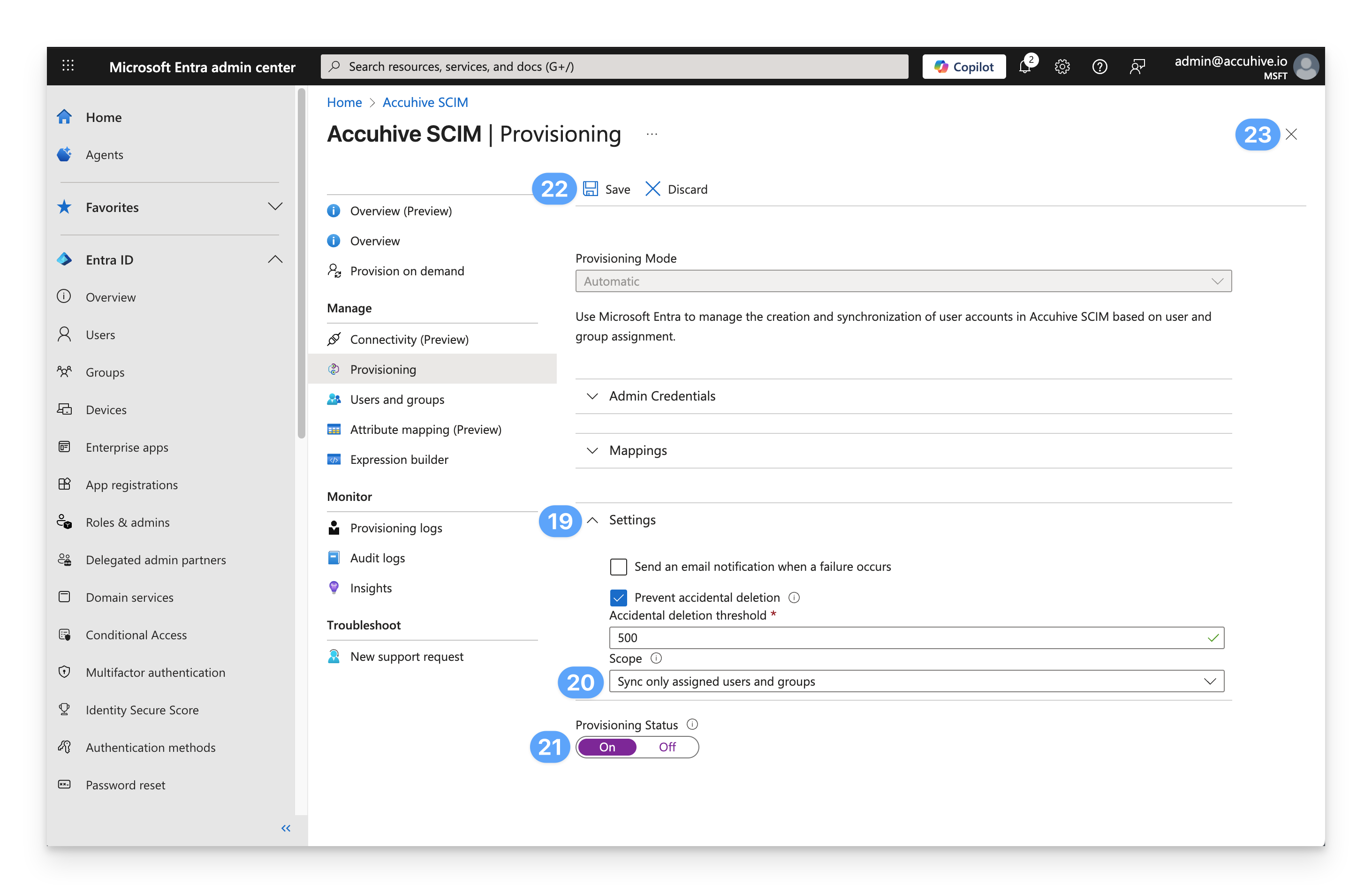
Expand the Settings reveal triangle.
For Scope, choose Sync only assigned users and groups.
Set the Provisioning Status to On.
Click Save.
Click the X in the upper-right corner to close the settings.
Assign Users and Groups
Under Manage, select Users and groups.
On the menu, select Add user/group.
.png)
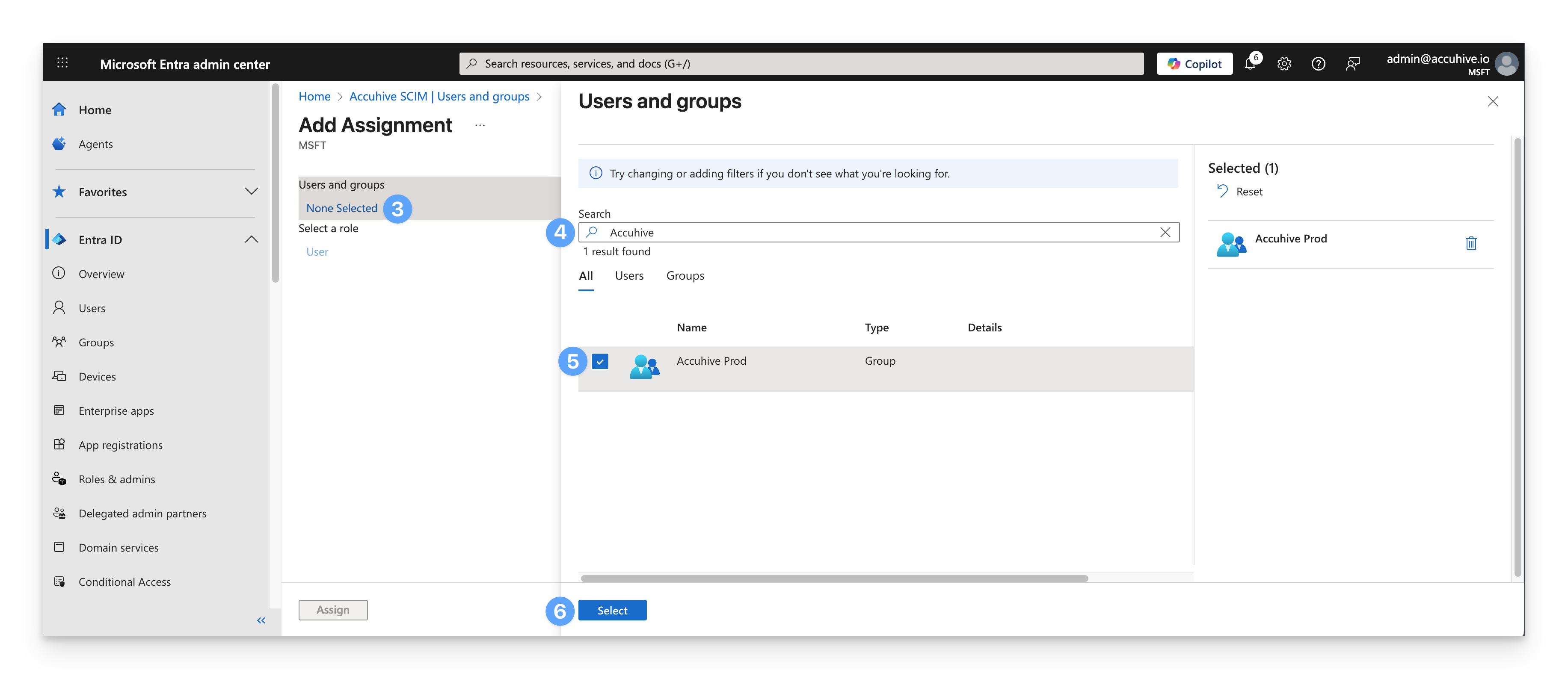
On the Add Assignment dialog, select the link under Users and groups.
A list of users and security groups is displayed. You can search for a specific user or group or select multiple users and groups that appear in the list.
Select the user(s) and group(s) you would like to be assigned.
Click Select.
 If you see the message below, it means that a free tier is being used, which means you can only add users (not groups) to the SCIM Enterprise App.
If you see the message below, it means that a free tier is being used, which means you can only add users (not groups) to the SCIM Enterprise App.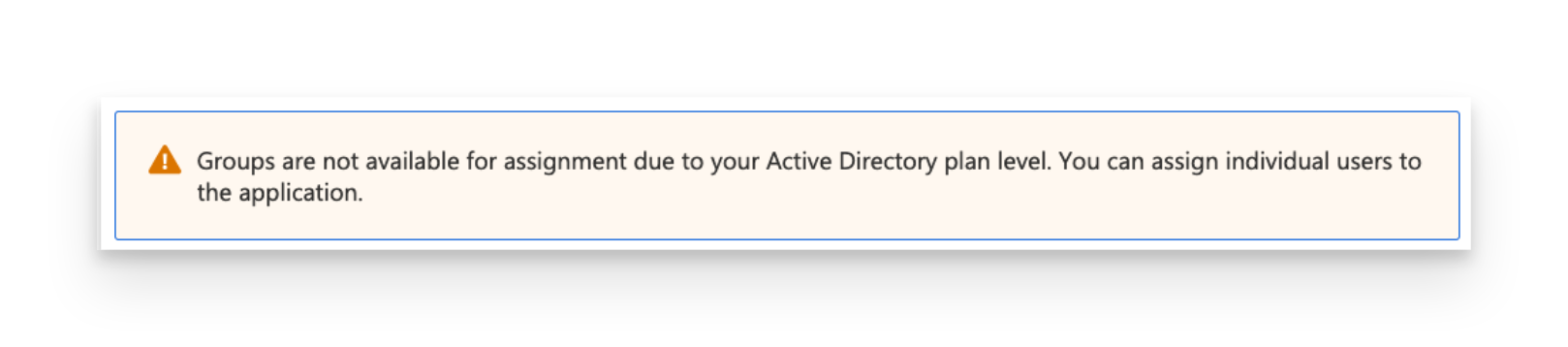
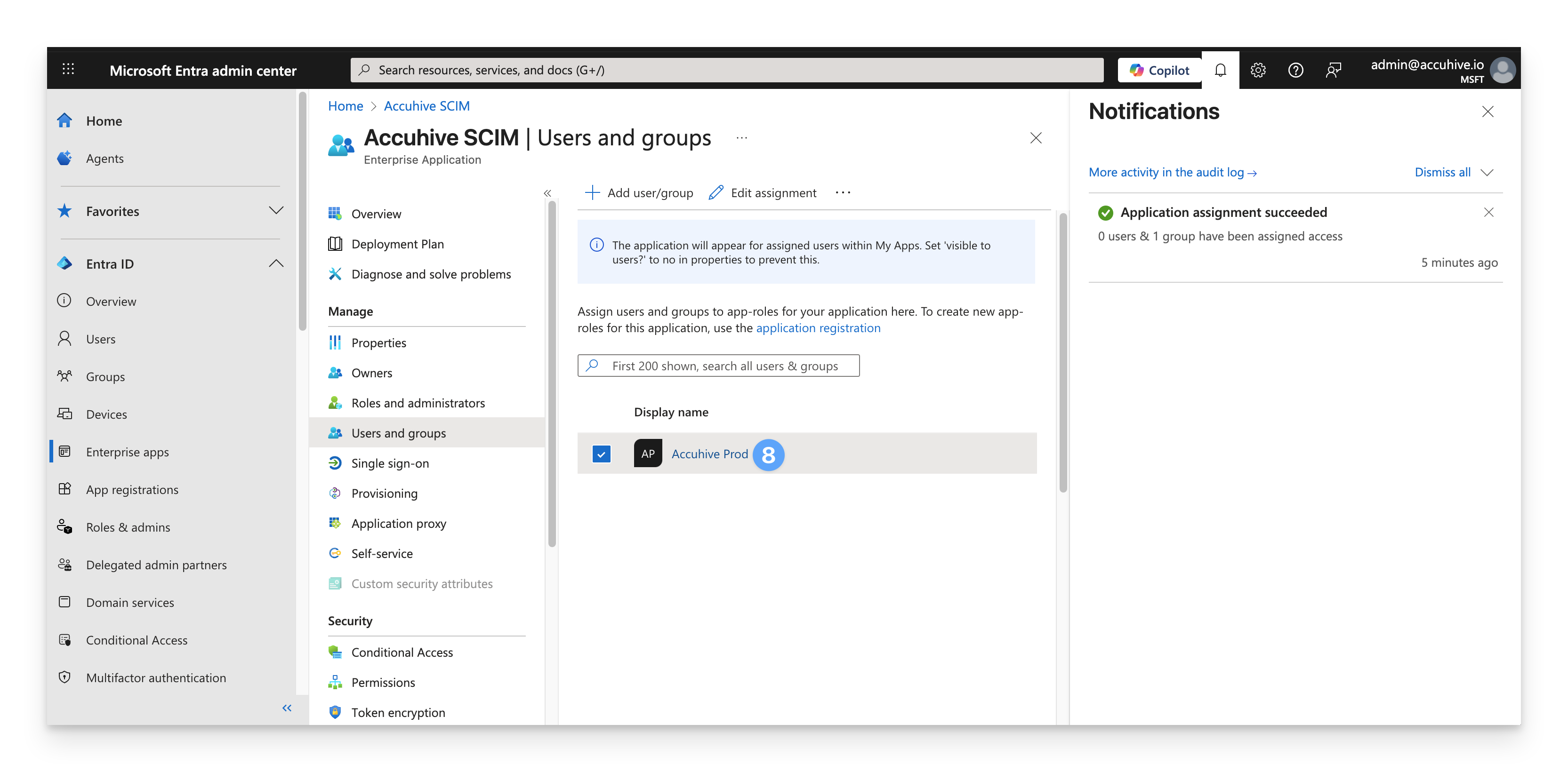
Select Assign to finish assigning users and groups to the app.
.png)
Confirm that the users and groups you added appear in the Users and groups list.
Considerations
AD CS Strong Certificate Mapping
When using Active Directory Certificate Services (AD CS), authentication will fail if a certificate can't be strongly mapped to an Active Directory account. Follow the steps below to enable Strong Certificate Mapping for your directory integration.
Access Your SCIM App
Go to the Microsoft Entra ID Admin Portal
Navigate to Applications > Enterprise Applications
Find and open the SCIM app you're using with Kandji
Configure Provisioning
Under Manage, click Provisioning
Under Manage, click Attribute Mapping (Preview)
Select Provision Microsoft Entra ID Users
Add the Security Identifier Attribute
Scroll to the bottom of the page
Check the box to show advanced options
Click Edit attribute list for <customappsso>
Add a new field called
onPremisesSecurityIdentifier, leaving the default type as String.Click Save
Map the Attribute
Go back to the Attribute Mapping section
Scroll down and click Add New Mapping
Keep Mapping type set to Direct
Set Source attribute to
onPremisesSecurityIdentifierSet Target attribute to
onPremisesSecurityIdentifierClick OK, then Save
The onPremisesSecurityIdentifier will show up in your user attributes in Kandji after the next Entra SCIM sync (every 20-40 minutes).
Syncing
User syncing is one-way, meaning the Microsoft Entra ID SCIM app will send user information to Kandji only when new information is needed.If a user or group is added to the SCIM app in Microsoft Entra ID after the app was created, a sync will happen every 40 minutes (set by Microsoft Entra ID). If you want the sync to happen sooner, you can stop/start the provisioning in the SCIM app on the Microsoft Entra ID. This will not impact existing users/groups in Kandji.
Removing Users
If Entra ID sends sets a use to inactive, the user will be set as inactive in your Kandji tenant.
If Entra ID deletes a user, the user will be deleted from your Kandji tenant.
Blueprint Conditional Logic
If you use Assignment Map conditional logic with groups, you must explicitly add each group you want to have provisioned in Kandji to the SCIM app. Groups will not sync automatically by adding users that happen to be members of the group.
Microsoft Device Compliance
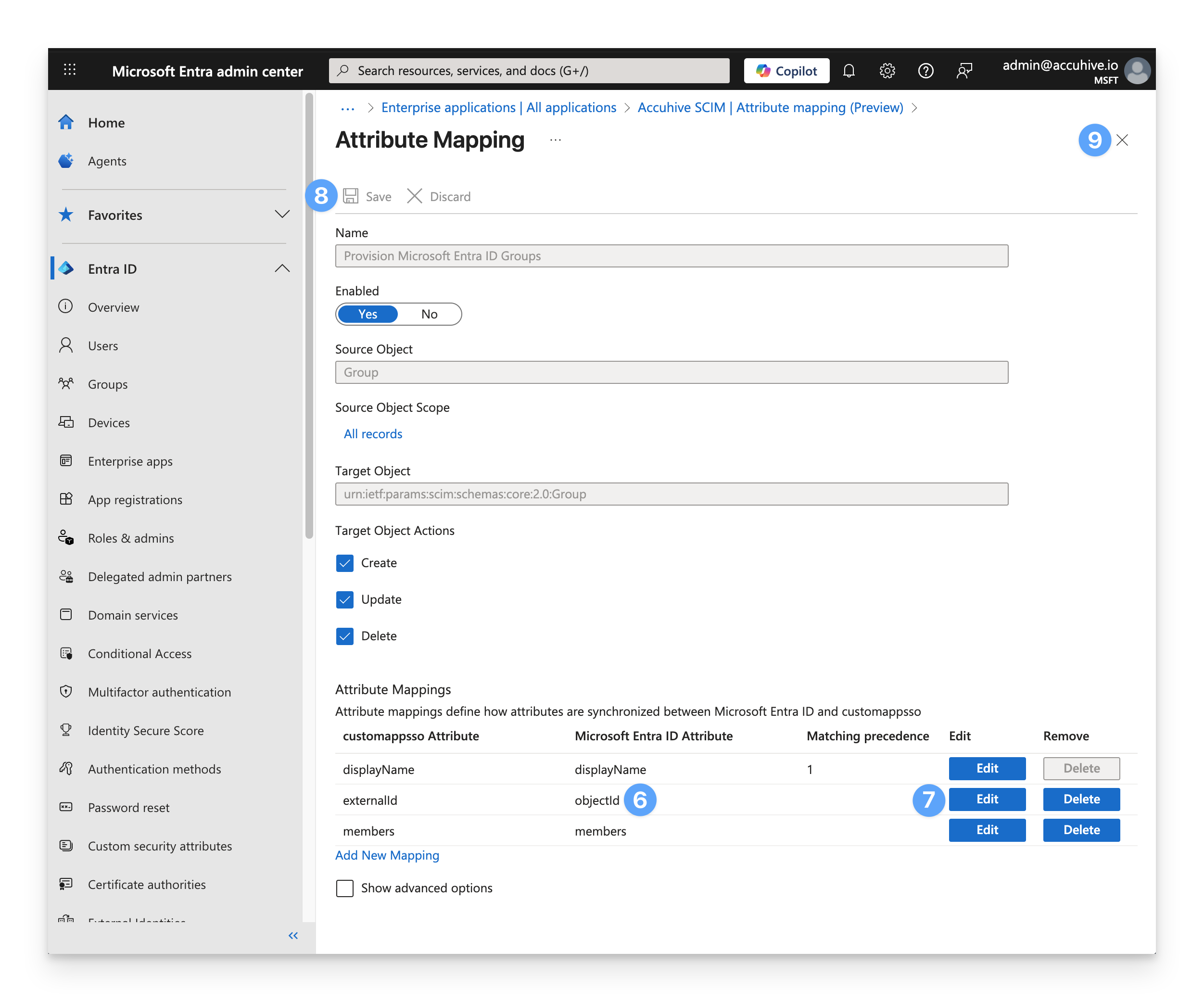
If you are using an Entra ID SCIM user directory integration and the Microsoft Device Compliance integration ensure that the user and group attribute mappings for the externalId attribute in your SCIM application map to objectId as listed below. The objectId is used by Kandji to map user and group resources in Intune.
User Attribute | User Value |
|---|---|
externalId | objectId |
Group Attribute | Group Value |
|---|---|
externalId | objectId |
Updating user mappings and group mappings
Navigate to the SCIM enterprise application in the Microsoft Entra admin center.
Select Provisioning.
Select the Attribute mapping (Preview) section.
If you are updating user attributes, click on Provision Microsoft Entra ID Users.
If you are updating group attributes, click on Provision Microsoft Entra ID Groups.
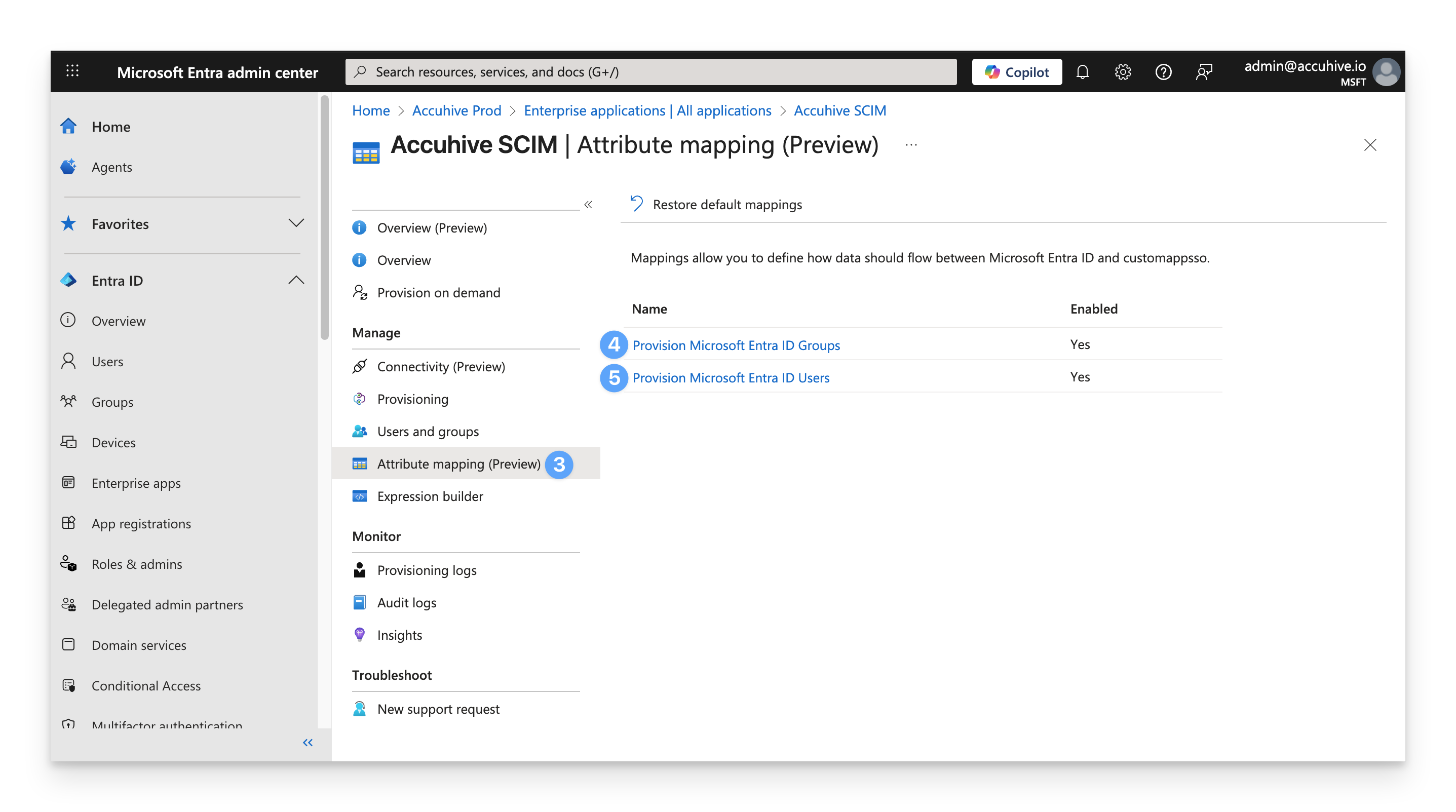
Verify that externalId is mapped to objectId.
If it is not, click the Edit button to the right of the attribute and select objectId from the list.
Click Save.
Click the X to go back.
Once back on the Provisioning overview page, if any values were changed, you need to push the updated values to Kandji immediately by stopping and then starting the provisioning service.
Click the Pause provisioning button.
Click the Start provisioning button.